
It’s been a month since I wrote Part 1 of “Bob and Alice in Kernel-land”. As expected, we saw minimal constructive feedback from vendors, with a few notable exceptions. Sophos provided the most detailed information about their drivers, while CrowdStrike offered valuable insights into their kernel architecture, including the use of Microsoft’s Winsock kernel file transfer. This feature, introduced in Windows Vista+, was designed to replace the outdated Transport Driver Interface (TDI). It’s reasonable to assume that the existence of this capability has significantly contributed to more operations being moved to kernel mode, as leveraging TDI posed considerable challenges without compromising stability.
The timing is particularly noteworthy given that CVE-2024-38193 (CVSS score: 7.8), a local privilege escalation vulnerability in a WinSock-related driver (afd.sys), has been reported this week to have being exploited in the wild by North Korea. Additionally, a new patch has been released for CVE-2024-38063 (CVSS 9.8), discovered by Wei from Kunlun Lab. This underscores the significant challenges in keeping the kernel network stack secure.
MSRC fixed a RCE bug in TCPIP module.
— wei (@XiaoWei___) August 14, 2024
I found the bug several months ago.
Its score is 9.8 and exploitation is more likely. Please apply the patch immediately. pic.twitter.com/bdjBLgoaYv
Endpoint Security Vendors 🔗
“Attackers think about attack vectors, Defenders think about market shares." - msuiche
This week, Microsoft Threat Protection CVP released an article featuring a pie chart that ranks Microsoft as the leader in “modern endpoint security market share,” according to the latest IDC report.
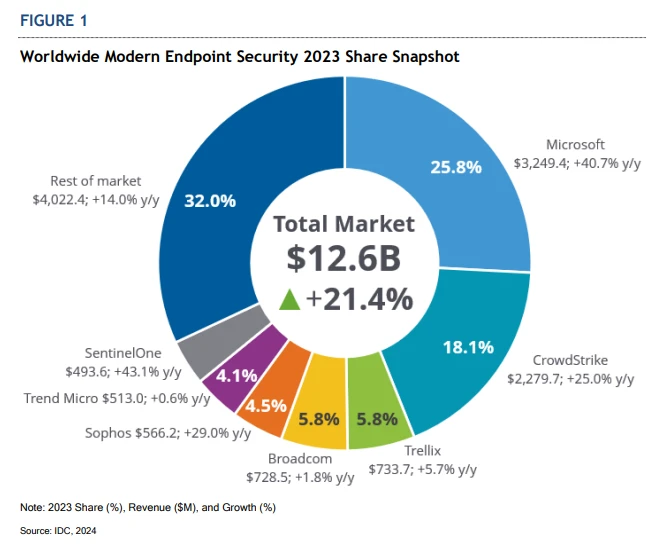
This leads to the question: How many “endpoint security vendors” are actually out there?
It’s challenging to answer this question using only Crunchbase and PitchBook. However, as I mentioned in Part 1, most endpoint security vendors need kernel access, often achieved through a minifilter driver. We can obtain an approximate list of these drivers from the Microsoft website, as discussed in my blog post regarding altitude allocation. However, this list “only” includes drivers that have requested a file system filter altitude.
An over-crowded space 🔗
I’ve compiled all the Microsoft filter allocation into a publicly available spreadsheet, available here: https://docs.google.com/spreadsheets/d/16PmB3aYTVow1PTxoJUZ8oDMrRyzLN7thOeHqojTVD4s/edit?usp=sharing
| Filter Type | Company | COUNTA of Minifilter | COUNTUNIQUE of Company |
|---|---|---|---|
| *FSFilter Imaging Total | 3 | 3 | |
| Filter Total | 2 | 1 | |
| FSFilter Activity Monitor Total | 772 | 475 | |
| FSFilter Anti-Virus Total | 379 | 202 | |
| FSFilter Bottom Total | 26 | 14 | |
| FSFilter Cluster File System Total | 4 | 4 | |
| FSFilter Compression Total | 11 | 9 | |
| FSFilter Content Screener Total | 157 | 122 | |
| FSFilter Continuous Backup Total | 45 | 40 | |
| FSFilter Copy Protection Total | 32 | 27 | |
| FSFilter Encryption Total | 178 | 154 | |
| FSFilter HSM Total | 93 | 65 | |
| FSFilter Open File Total | 9 | 9 | |
| FSFilter Physical Quota Management Total | 3 | 3 | |
| FSFilter Quota Management Total | 5 | 4 | |
| FSFilter Replication Total | 39 | 33 | |
| FSFilter Security Bottom Total | 1 | 1 | |
| FSFilter Security Content Screener Total | 1 | 1 | |
| FSFilter Security Enhancer Total | 143 | 102 | |
| FSFilter Security Monitor Total | 1 | 1 | |
| FSFilter System Total | 1 | 1 | |
| FSFilter System Recovery Total | 11 | 10 | |
| FSFilter Top Total | 54 | 38 | |
| FSFilter Undelete Total | 20 | 15 | |
| FSFilter Virtualization Total | 79 | 58 | |
| Grand Total | 2069 | 1130 |
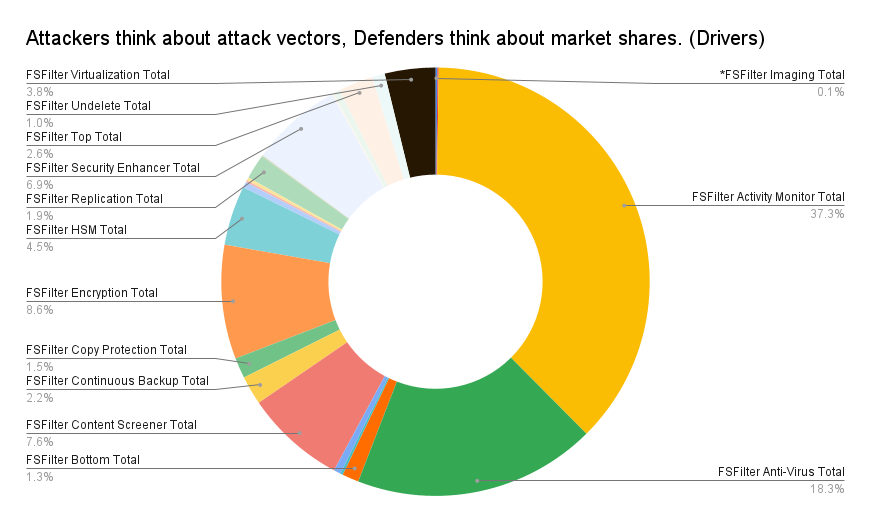
If we take the following categories:
- FSFilter Activity Monitor Total
- FSFilter Anti-Virus Total
- FSFilter Copy Protection Total
- FSFilter Encryption Total
- FSFilter HSM Total
- FSFilter Security Bottom Total
- FSFilter Security Content Screener Total
- FSFilter Security Enhancer Total
- FSFilter Security Monitor Total
- FSFilter System Recovery Total
At least 1,608 out of 2,069 drivers are associated with security products, including at least 1,152 drivers (Activity Monitor + Anti-Virus) used for endpoint security from a staggering 637 endpoint security vendors.
Conclusion 🔗
There are far more players in this space than I ever anticipated. Whether this is positive or negative remains to be seen (jk we know the answer), but I hope this list proves useful for those needing to identify which of their enrolled products use kernel drivers for risk and compliance purposes. Unfortnatutely, I don’t have the equivalent data for macOS and Linux.
P.S. A friend shared this analysis of 1,474 CVEs from Microsoft MSRC, covering Windows 10 x64 from January 2021 to August 2024, obtained through the Microsoft CVRF API. It’s another great example that emphasize again the difference in mindset: “Attackers focus on attack vectors, while defenders think about market shares”.